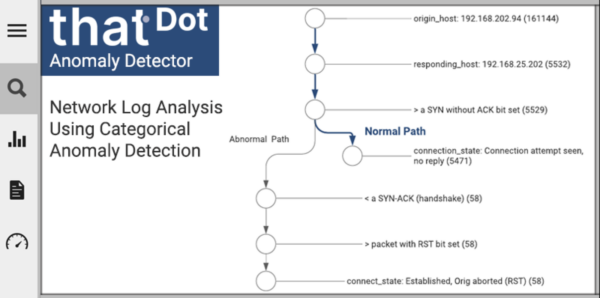
Network Log Analysis Using Categorical Anomaly Detection
The distributed nature of modern virtualized software architectures has created added complexity in the networking stack, making it difficult to attribute behavior to any single service.

The distributed nature of modern virtualized software architectures has created added complexity in the networking stack, making it difficult to attribute behavior to any single service.
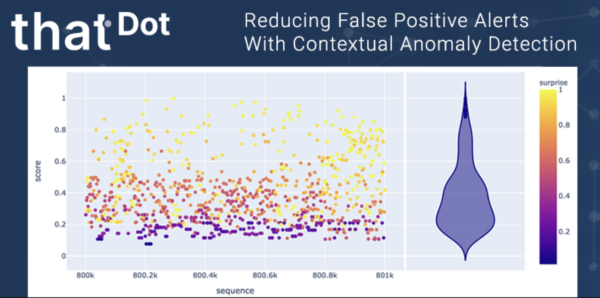
Traditionally, monitoring alerts are produced comparing metrics against thresholds to identify behavior outside the norm.
As crypto currencies go mainstream, better techniques for protecting users from fraud are needed. Enter streaming graph.
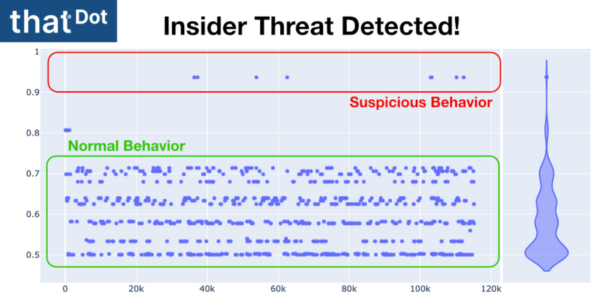
Advanced: Finding a malicious employee is one of the toughest cyber-security challenges in the industry.

The move to the cloud represents new challenges for enterprise security teams. Use thatDot Novelty Detector to detect the attack quickly.

thatDot’s real-time Novelty Detector for categorical has updated its data exploration and data transformation capabilities.